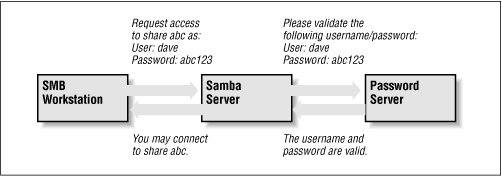
Server-level security is similar to user-level security. However, with server-level security, Samba delegates password authentication to another SMB password server, typically another Samba server or a Windows NT Server acting as a PDC on the network. Note that Samba still maintains its list of shares and their configuration in its
smb.conf file. When a client attempts to make a connection to a particular share, Samba validates that the user is indeed authorized to connect to the share. Samba will then attempt to validate the password by contacting the SMB password server through a known protocol and presenting the username and password to the SMB password server. If the password is accepted, a session will be established with the client. See
Figure 6.2 for an illustration of this setup.
You can configure Samba to use a separate password server under server-level security with the use of the
password
server global configuration option, as follows:
[global]
security = server
password server = PHOENIX120 HYDRA134
Note that you can specify more than one machine as the target of the
password
server ; Samba will move down the list of servers in the event that its first choice is unreachable. The servers identified by the
password
server option are given as NetBIOS names, not their DNS names or equivalent IP addresses. Also, if any of the servers reject the given password, the connection will automatically fail - Samba will not attempt another server.
One caveat: when using this option, you will still need an account representing that user on the regular Samba server. This is because the Unix operating system needs a username to perform various I/O operations. The preferable method of handling this is to give the user an account on the Samba server but disable the account's password by replacing it in the system password file (e.g.,
/etc/passwd ) with an asterisk (*).
