With share-level security, each share has one or more passwords associated with it. This differs from the other modes of security in that there are no restrictions as to whom can access a share, as long as that individual knows the correct password. Shares often have multiple passwords. For example, one password may grant read-only access, while another may grant read-write access, and so on. Security is maintained as long as unauthorized users do not discover the password for a share to which they shouldn't have access.
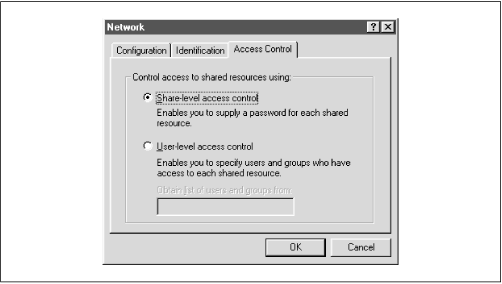
OS/2 and Window 95/98 both support share-level security on their resources. You can set up share-level security with Windows 95/98 by first enabling share-level security using the Access Control tab of the Network Control Panel dialog. Then select the Share-level Access Control radio button (which deselects the user-level access control radio button), as shown in
Figure 6.1, and press the OK button.
Next, right click on a resource - such as a hard drive or a CD-ROM - and select the Properties menu item. This will bring up the Resource Properties dialog box. Select the Sharing tab at the top of the dialog box and enable the resource as Shared As. From here, you can configure how the shared resource will appear to individual users, as well as assigning whether the resource will appear as read-only, read-write, or a mix, depending on the password that is supplied.
You might be thinking that this security model is not a good fit for Samba - and you would be right. In fact, if you set the
security
=
share option in the Samba configuration file, Samba will still reuse the username/passwords combinations in the system password files to authenticate access. More precisely, Samba will take the following steps when a client requests a connection using share-level security:
-
When a connection is requested, Samba will accept the password and (if sent) the username of the client.
-
If the share is
guest
only , the user is immediately granted access to the share with the rights of the user specified by the
guest
account parameter; no password checking is performed.
-
For other shares, Samba appends the username to a list of users who are allowed access to the share. It then attempts to validate the password given in association with that username. If successful, Samba grants the user access to the share with the rights assigned to that user. The user will not need to authenticate again unless a
revalidate
=
yes option has been set inside the share.
-
If the authentication is unsuccessful, Samba will attempt to validate the password against the list of users it has previously compiled throughout the attempted connections, as well as any specified under the share in the configuration file. If the password does not match any usernames (as specified in the system password file, typically
/etc/passwd ), the user is not granted access to the share under that username.
-
However, if the share has a
guest
ok or
public option set, the user will default to access with the rights of the user specified by the
guest
account option.
You can indicate in the configuration file which users should be initially placed on the share-level security user list by using the
username configuration option, as shown below:
[global]
security = share
[accounting1]
path = /home/samba/accounting1
guest ok = no
writable = yes
username = davecb, pkelly, andyo
Here, when a user attempts to connect to a share, Samba will verify the password that was sent against each of the users in its own list, in addition to the passwords of users
davecb,
pkelly, and
andyo. If any of the passwords match, the connection will be verified and the user will be allowed. Otherwise, connection to the specific share will fail.
