Basic Concepts of Trusted Extensions
Trusted Extensions software adds labels to a Solaris system. Labeled desktops and trusted
applications, such as the Label Builder and the Device Allocation Manager, are also
added. The concepts in this section are necessary to understand Trusted Extensions, both
for users and administrators. Users are introduced to these concepts in the Solaris Trusted Extensions User’s Guide.
Trusted Extensions Protections
Trusted Extensions software enhances the protection of the Solaris OS. The Solaris
OS protects access to the system with user accounts that require passwords. You
can require that passwords be changed regularly, be of a certain length, and
so on. Roles require additional passwords to perform administrative tasks. Additional authentication limits the
damage that can be done by an intruder who guesses the root
password, because roles cannot be used as login accounts. Trusted Extensions software goes further
by restricting users and roles to an approved label range. This label range
limits the information that users and roles can access.
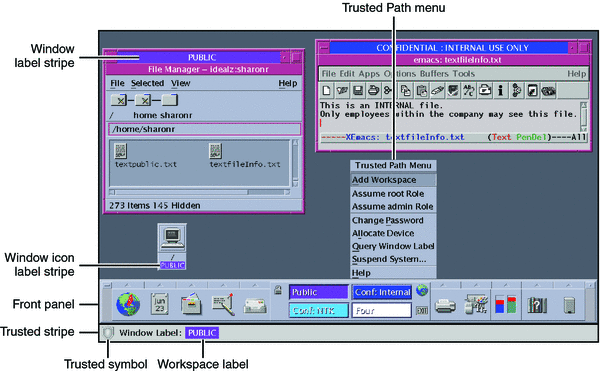
Trusted Extensions software displays the Trusted Path symbol, an unmistakable, tamper-proof emblem that
appears at the left of the trusted stripe. In Trusted CDE, the stripe
is at the bottom of the screen. In Trusted GNOME, the stripe is
at the top of the screen. The Trusted Path symbol indicates to users
when they are using security-related parts of the system. If this symbol does
not appear when the user is running a trusted application, that version of
the application should be checked immediately for authenticity. If the trusted stripe does
not appear, the desktop is not trustworthy. For a sample desktop display, see
Figure 7-1.
Figure 7-1 Trusted Extensions Multilevel CDE Desktop
Most security-related software, that is, the Trusted Computing Base (TCB), runs in the
global zone. Regular users cannot enter the global zone or view its resources.
Users are able to interact with TCB software, as in when they change
passwords. The Trusted Path symbol is displayed whenever the user interacts with the
TCB.
Trusted Extensions and Access Control
Trusted Extensions software protects information and other resources through both discretionary access control
(DAC) and mandatory access control (MAC). DAC is the traditional UNIX permission bits
and access control lists that are set at the discretion of the owner.
MAC is a mechanism that the system enforces automatically. MAC controls all transactions
by checking the labels of processes and data in the transaction.
A user's label represents the sensitivity level at which the user is permitted
to operate and chooses to operate. Typical labels are Secret, or Public. The
label determines the information that the user is allowed to access. Both MAC
and DAC can be overridden by special permissions that are in the Solaris
OS. Privileges are special permissions that can be granted to processes. Authorizations
are special permissions that can be granted to users and roles by an
administrator.
As an administrator, you need to train users on the proper procedures for
securing their files and directories, according to your site's security policy. Furthermore, you
need to instruct any users who are allowed to upgrade or downgrade labels
as to when doing so is appropriate.
Roles and Trusted Extensions
On a system that is running Solaris software without Trusted Extensions, roles are
optional. On a system that is configured with Trusted Extensions, roles are required.
The system is administered by the System Administrator role and the Security Administrator
role. In some cases, the root role is used.
As in the Solaris OS, rights profiles are the basis of a
role's capabilities. Trusted Extensions provides two rights profiles, Information Security and User Security.
These two profiles define the Security Administrator role.
The programs that are available to a role in Trusted Extensions have a
special property, the trusted path attribute. This attribute indicates that the program is part of
the TCB. The trusted path attribute is available when a program is launched
from the global zone.
For information about roles, see Part III, Roles, Rights Profiles, and Privileges, in System Administration Guide: Security Services.
Labels in Trusted Extensions Software
Labels and clearances are at the center of mandatory access control (MAC) in
Trusted Extensions. They determine which users can access which programs, files, and directories.
Labels and clearances consist of one classification component and zero or more
compartment components. The classification component indicates a hierarchical level of security such as TOP SECRET
or CONFIDENTIAL. The compartment component represents a group of users who might need
access to a common body of information. Some typical types of compartments are
projects, departments, or physical locations. Labels are readable by authorized users, but internally, labels
are manipulated as numbers. The numbers and their readable versions are defined in
the label_encodings file.
Trusted Extensions mediates all attempted security-related transactions. The software compares the labels of
the accessing entity, typically a process, and the entity being accessed, usually a
filesystem object. The software then permits or disallows the transaction depending on which
label is dominant. Labels are also used to determine access to other
system resources, such as allocatable devices, networks, frame buffers, and other hosts.
Dominance Relationships Between Labels
One entity's label is said to dominate another label if the following two
conditions are met:
The classification component of the first entity's label is equal to or higher than the second entity's classification. The security administrator assigns numbers to classifications in the label_encodings file. The software compares these numbers to determine dominance.
The set of compartments in the first entity includes all of the second entity's compartments.
Two labels are said to be equal if they have the same classification
and the same set of compartments. If the labels are equal, they dominate
each other and access is permitted.
If one label has a higher classification or if it has the
same classification and its compartments are a superset of the second label's compartments,
or both, the first label is said to strictly dominate the second label.
Two labels are said to be disjoint or noncomparable if neither label
dominates the other label.
The following table presents examples of label comparisons for dominance. In the example,
NEED_TO_KNOW is a higher classification than INTERNAL. There are three compartments: Eng, Mkt, and
Fin.
Table 7-1 Examples of Label Relationships
Label 1 |
Relationship |
Label 2 |
|---|
NEED_TO_KNOW Eng Mkt |
(strictly) dominates |
INTERNAL Eng Mkt |
NEED_TO_KNOW Eng Mkt |
(strictly) dominates |
NEED_TO_KNOW Eng |
NEED_TO_KNOW Eng Mkt |
(strictly) dominates |
INTERNAL Eng |
NEED_TO_KNOW Eng Mkt |
dominates (equals) |
NEED_TO_KNOW Eng Mkt |
NEED_TO_KNOW Eng Mkt |
is disjoint with |
NEED_TO_KNOW Eng Fin |
NEED_TO_KNOW Eng Mkt |
is disjoint with |
NEED_TO_KNOW Fin |
NEED_TO_KNOW Eng Mkt |
is disjoint
with |
INTERNAL Eng Mkt Fin |
Administrative Labels
Trusted Extensions provides two special administrative labels that are used as labels or
clearances: ADMIN_HIGH and ADMIN_LOW. These labels are used to protect system resources and
are intended for administrators rather than regular users.
ADMIN_HIGH is the highest label. ADMIN_HIGH dominates all other labels in the system
and is used to protect system data, such as administration databases or audit
trails, from being read. You must be in the global zone to read
data that is labeled ADMIN_HIGH.
ADMIN_LOW is the lowest label. ADMIN_LOW is dominated by all other labels in a
system, including labels for regular users. Mandatory access control does not permit users
to write data to files with labels lower than the user's label. Thus,
a file at the label ADMIN_LOW can be read by regular users, but
cannot be modified. ADMIN_LOW is typically used to protect public executables that are
shared, such as files in /usr/bin.
Label Encodings File
All label components for a system, that is, classifications, compartments, and the associated
rules, are stored in an ADMIN_HIGH file, the label_encodings file. This file is
located in the /etc/security/tsol directory. The security administrator sets up the label_encodings file
for the site. A label encodings file contains:
Component definitions – Definitions of classifications, compartments, labels, and clearances, including rules for required combinations and constraints
Accreditation range definitions – Specification of the clearances and minimum labels that define the sets of available labels for the entire system and for regular users
Printing specifications – Identification and handling information for print banners, trailers, headers, footers, and other security features on printer output
Customizations – Local definitions including label color codes, and other defaults
For more information, see the label_encodings(4) man page. Detailed information can also be
found in Solaris Trusted Extensions Label Administration and Compartmented Mode Workstation Labeling: Encodings Format.
Label Ranges
A label range is the set of potentially usable labels at which users can
operate. Both users and resources both have label ranges. Resources that can be
protected by label ranges include such things as allocatable devices, networks, interfaces, frame
buffers, and commands or actions. A label range is defined by a
clearance at the top of the range and a minimum label at
the bottom.
A range does not necessarily include all combinations of labels that fall between
a maximum and minimum label. Rules in the label_encodings file can disqualify certain
combinations. A label must be well-formed, that is, permitted by all applicable rules
in the label encodings file, in order to be included in a range.
However, a clearance does not have to be well-formed. Suppose, for example, that
a label_encodings file prohibits any combination of compartments Eng, Mkt, and Fin in a
label. INTERNAL Eng Mkt Fin would be a valid clearance but not a valid label. As
a clearance, this combination would let a user access files that are labeled
INTERNAL Eng, INTERNAL Mkt, and INTERNAL Fin.
Account Label Range
When you assign a clearance and a minimum label to a user,
you define the upper and lower boundaries of the account label range in which that user
is permitted to operate. The following equation describes the account label range, using
≤ to indicate “dominated by or the same as”:
minimum label ≤ permitted label ≤ clearance
Thus, the user is permitted to operate at any label that is
dominated by the clearance as long as that label dominates the minimum label.
When a user's clearance or minimum label is not expressly set, the defaults
that are defined in the label_encodings file take effect.
Users can be assigned a clearance and a minimum label that enable them
to operate at more than one label, or at a single label. When
a user's clearance and minimum label are equal, the user can operate at
only one label.
Session Range
The session range is the set of labels that is available to a user
during a Trusted Extensions session. The session range must be within the user's
account label range and the label range set for the system. At login,
if the user selects single-label session mode, the session range is limited to
that label. If the user selects multilabel session mode, then the label that
the user selects becomes the session clearance. The session clearance defines the upper
boundary of the session range. The user's minimum label defines the lower bound.
The user begins the session in a workspace at the minimum label. During
the session, the user can switch to a workspace at any label within
the session range.
What Labels Protect and Where Labels Appear
Labels appear on the desktop and on output that is executed on
the desktop, such as printer output.
Applications – Applications start processes. These processes run at the label of the workspace where the application is started. An application in a labeled zone, as a file, is labeled at the label of the zone.
Devices – Data flowing through devices is controlled through device allocation and device label ranges. To use a device, users must be within the label range of the device, and be authorized to allocate the device.
File system mount points – Every mount point has a label. The label is viewable by using the getlabel command.
Network interfaces – IP addresses (hosts) have templates that describe their label range. Unlabeled hosts also have a default label.
Printers and printing – Printers have label ranges. Labels are printed on body pages. Labels, handling information, and other security information is printed on the banner and trailer pages. To configure printing in Trusted Extensions, see Chapter 21, Managing Labeled Printing (Tasks) and Labels on Printed Output in Solaris Trusted Extensions Label Administration.
Processes – Processes are labeled. Processes run at the label of the workspace where the process originates. The label of a process is visible by using the plabel command.
Users – Users are assigned a default label and a label range. The label of the user's workspace indicates the label of the user's processes.
Windows – Labels are visible at the top of desktop windows. The label of the desktop is also indicated by color. The color appears on the desktop switch and above window title bars.
When a window is moved to a differently labeled workspace, the window maintains its original label.
Zones – Every zone has a unique label. The files and directories that are owned by a zone are at the zone's label. For more information, see the getzonepath(1) man page.
