PAM (Overview)
The Pluggable Authentication Module (PAM) framework lets you “plug in” new authentication services
without changing system entry services, such as login, ftp, and telnet. You can also
use PAM to integrate UNIX login with other security mechanisms such as Kerberos.
Mechanisms for account, credential, session, and password management can also be “plugged
in” by using this framework.
Benefits of Using PAM
The PAM framework enables you to configure the use of system entry
services (such as, ftp, login, telnet, or rsh) for user authentication. Some benefits
that PAM provides are as follows:
Flexible configuration policy
Per-application authentication policy
The ability to choose a default authentication mechanism
The ability to require multiple authorizations on high-security systems
Ease of use for the end user
No retyping of passwords if the passwords are the same for different authentication services
The ability to prompt the user for passwords for multiple authentication services without requiring the user to type multiple commands
The ability to pass optional options to the user authentication services
The ability to implement a site-specific security policy without having to change the system entry services
Introduction to the PAM Framework
The PAM framework consists of four parts:
The framework provides a uniform way for authentication-related activities to take place. This
approach enables application developers to use PAM services without having to know the
semantics of the policy. Algorithms are centrally supplied. The algorithms can be modified independently
of the individual applications. With PAM, administrators can tailor the authentication process to
the needs of a particular system without having to change any applications. Adjustments
are made through pam.conf, the PAM configuration file.
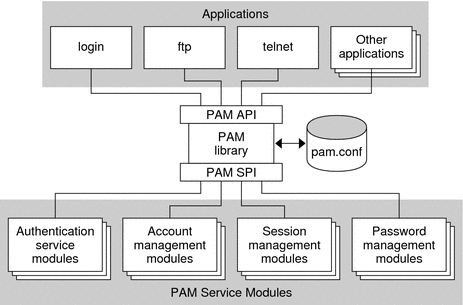
The following figure illustrates the PAM architecture. Applications communicate with the PAM library
through the PAM application programming interface (API). PAM modules communicate with the PAM
library through the PAM service provider interface (SPI). Thus, the PAM library enables
applications and modules to communicate with each other.
Figure 17-1 PAM Architecture
Changes to PAM for the Solaris 10 Release
The Solaris 10 release includes the following changes to the Pluggable Authentication Module
(PAM) framework:
The pam_authtok_check module now allows for strict password checking using new tunable parameters in the /etc/default/passwd file. The new parameters define:
A list of comma separated dictionary files used for checking common dictionary words in a password
The minimum differences required between a new password and an old password
The minimum number of alphabetic or nonalphabetic characters that must be used in a new password
The minimum number of uppercase or lowercase letters that must be used in a new password
The number of allowable consecutive repeating characters
The pam_unix_auth module implements account locking for local users. Account locking is enabled by the LOCK_AFTER_RETRIES parameter in /etc/security/policy.conf and the lock_after-retries key in /etc/user_attr. See the policy.conf(4) and the user_attr(4) man pages for more information.
A new binding control flag has been defined. This control flag is documented in the pam.conf(4) man page and in How PAM Stacking Works.
The pam_unix module has been removed and replaced by a set of service modules of equivalent or greater functionality. Many of these modules were introduced in the Solaris 9 release. Here is a list of the replacement modules:
pam_authtok_check
pam_authtok_get
pam_authtok_store
pam_dhkeys
pam_passwd_auth
pam_unix_account
pam_unix_auth
pam_unix_cred
pam_unix_session
The functionality of the pam_unix_auth module has been split into two modules. The pam_unix_auth module now verifies that the password is correct for the user. The new pam_unix_cred module provides functions that establish user credential information.
Additions to the pam_krb5 module have been made to manage the Kerberos credentials cache using the PAM framework.
A new pam_deny module has been added. The module can be used to deny access to services. By default, the pam_deny module is not used. For more information, see the pam_deny(5) man page.
Changes to PAM for the Solaris Express 1/06 Release
The PAM framework for the Solaris Express 1/06 release includes a new
pam_allow module. The module can be used to grant access to all users,
without enforcing any security. The module should be used with caution. For more
information, see the pam_allow(5) man page.
