Configuring Resource Controls and Attributes
The resource controls facility is configured through the project database. See Chapter 2, Projects and Tasks (Overview). Resource controls
and other attributes are set in the final field of the project
database entry. The values associated with each resource control are enclosed in parentheses,
and appear as plain text separated by commas. The values in parentheses constitute
an “action clause.” Each action clause is composed of a privilege level, a
threshold value, and an action that is associated with the particular threshold. Each
resource control can have multiple action clauses, which are also separated by commas. The
following entry defines a per-task lightweight process limit and a per-process maximum CPU
time limit on a project entity. The process.max-cpu-time would send a process
a SIGTERM after the process ran for 1 hour, and a SIGKILL if
the process continued to run for a total of 1 hour and
1 minute. See Table 6-3.
development:101:Developers:::task.max-lwps=(privileged,10,deny);
process.max-cpu-time=(basic,3600,signal=TERM),(priv,3660,signal=KILL)
typed as one line
Note - On systems that have zones enabled, zone-wide resource controls are specified in the
zone configuration using a slightly different format. See Zone Configuration Data for more information.
The rctladm command allows you to make runtime interrogations of and modifications to
the resource controls facility, with global scope. The prctl command allows you to
make runtime interrogations of and modifications to the resource controls facility, with local scope.
For more information, see Global and Local Actions on Resource Control Values, rctladm(1M) and prctl(1).
Note - On a system with zones installed, you cannot use rctladm in a non-global
zone to modify settings. You can use rctladm in a non-global zone to
view the global logging state of each resource control.
Available Resource Controls
A list of the standard resource controls that are available in this release
is shown in the following table.
The table describes the resource that is constrained by each control. The table
also identifies the default units that are used by the project database
for that resource. The default units are of two types:
Thus, project.cpu-shares specifies the number of shares to which the project is entitled.
process.max-file-descriptor specifies the highest file number that can be assigned to a process
by the open(2) system call.
Table 6-1 Standard Project, Task, and Process Resource Controls
Control Name |
Description |
Default Unit |
|---|
project.cpu-cap |
Absolute limit on the amount of
CPU resources that can be consumed by a project. A value of 100
means 100% of one CPU as the project.cpu-cap setting. A value of
125 is 125%, because 100% corresponds to one full CPU on the system
when using CPU caps. |
Quantity (number of CPUs) |
project.cpu-shares |
Number of CPU shares granted to
this project for use with the fair share scheduler (see FSS(7)). |
Quantity (shares) |
project.max-crypto-memory |
Total amount
of kernel memory that can be used by libpkcs11 for hardware crypto acceleration.
Allocations for kernel buffers and session-related structures are charged against this resource control. |
Size
(bytes) |
project.max-locked-memory |
Total amount of physical locked memory allowed. If priv_proc_lock_memory is assigned to a
user, consider setting this resource control as well to prevent that user from
locking all memory. Note that this resource control replaced project.max-device-locked-memory, which has been removed.
This release control will be removed in a future release. |
Size (bytes) |
project.max-msg-ids |
Maximum number of
message queue IDs allowed for this project. |
Quantity (message queue IDs) |
project.max-port-ids |
Maximum allowable number
of event ports. |
Quantity (number of event ports) |
project.max-sem-ids |
Maximum number of semaphore IDs
allowed for this project. |
Quantity (semaphore IDs) |
project.max-shm-ids |
Maximum number of shared memory IDs allowed
for this project. |
Quantity (shared memory IDs) |
project.max-shm-memory |
Total amount of System V shared memory
allowed for this project. |
Size (bytes) |
project.max-lwps |
Maximum number of LWPs simultaneously available to this
project. |
Quantity (LWPs) |
project.max-tasks |
Maximum number of tasks allowable in this project. |
Quantity (number of tasks) |
project.max-contracts |
Maximum
number of contracts allowed in this project. |
Quantity (contracts) |
task.max-cpu-time |
Maximum CPU time that is
available to this task's processes. |
Time (seconds) |
task.max-lwps |
Maximum number of LWPs simultaneously available to
this task's processes. |
Quantity (LWPs) |
process.max-cpu-time |
Maximum CPU time that is available to this process. |
Time
(seconds) |
process.max-file-descriptor |
Maximum file descriptor index available to this process. |
Index (maximum file descriptor) |
process.max-file-size |
Maximum file
offset available for writing by this process. |
Size (bytes) |
process.max-core-size |
Maximum size of a core
file created by this process. |
Size (bytes) |
process.max-data-size |
Maximum heap memory available to this process. |
Size
(bytes) |
process.max-stack-size |
Maximum stack memory segment available to this process. |
Size (bytes) |
process.max-address-space |
Maximum amount of address
space, as summed over segment sizes, that is available to this process. |
Size (bytes) |
process.max-port-events |
Maximum
allowable number of events per event port. |
Quantity (number of events) |
process.max-sem-nsems |
Maximum number
of semaphores allowed per semaphore set. |
Quantity (semaphores per set) |
process.max-sem-ops |
Maximum number of semaphore
operations allowed per semop call (value copied from the resource control at semget()
time). |
Quantity (number of operations) |
process.max-msg-qbytes |
Maximum number of bytes of messages on a message
queue (value copied from the resource control at msgget() time). |
Size (bytes) |
process.max-msg-messages |
Maximum number of
messages on a message queue (value copied from the resource control at msgget()
time). |
Quantity (number of messages) |
You can display the default values for resource controls on a system that
does not have any resource controls set or changed. Such a system
contains no non-default entries in /etc/system or the project database. To display values,
use the prctl command.
Zone-Wide Resource Controls
Zone-wide resource controls limit the total resource usage of all process entities within
a zone. Zone-wide resource controls can also be set using global property names
as described in Setting Zone-Wide Resource Controls and How to Configure the Zone.
Table 6-2 Zones Resource Controls
Control Name |
Description |
Default Unit |
|---|
zone.cpu-cap |
Absolute limit on the amount
of CPU resources that can be consumed by a non-global zone. A value
of 100 means 100% of one CPU as the project.cpu-cap setting. A value
of 125 is 125%, because 100% corresponds to one full CPU on the
system when using CPU caps. |
Quantity (number of CPUs) |
zone.cpu-shares |
Number of fair share scheduler (FSS)
CPU shares for this zone |
Quantity (shares) |
zone.max-locked-memory |
Total amount of physical locked memory available
to a zone. When priv_proc_lock_memory is assigned to a zone, consider setting this resource
control as well to prevent that zone from locking all memory. |
Size (bytes) |
zone.max-lwps |
Maximum number
of LWPs simultaneously available to this zone |
Quantity (LWPs) |
zone.max-msg-ids |
Maximum number of message queue
IDs allowed for this zone |
Quantity (message queue IDs) |
zone.max-sem-ids |
Maximum number of semaphore IDs
allowed for this zone |
Quantity (semaphore IDs) |
zone.max-shm-ids |
Maximum number of shared memory IDs allowed
for this zone |
Quantity (shared memory IDs) |
zone.max-shm-memory |
Total amount of System V shared memory
allowed for this zone |
Size (bytes) |
zone.max-swap |
Total amount of swap that can be consumed
by user process address space mappings and tmpfs mounts for this zone. |
Size (bytes) |
For information on configuring zone-wide resource controls, see Resource Type Properties and How to Configure the Zone. To
use zone-wide resource controls in lx branded zones, see How to Configure, Verify, and Commit the lx Branded Zone.
Note that it is possible to apply a zone-wide resource control to
the global zone. See Using the Fair Share Scheduler on a Solaris System With Zones Installed for additional information.
Units Support
Global flags that identify resource control types are defined for all resource controls.
The flags are used by the system to communicate basic type information to
applications such as the prctl command. Applications use the information to determine the
following:
The following global flags are available:
Global Flag |
Resource Control Type String |
Modifier |
Scale |
|---|
RCTL_GLOBAL_BYTES |
bytes |
B |
1 |
|
KB |
210 |
|
MB |
220 |
|
GB |
230 |
|
TB |
240 |
|
PB |
250 |
|
EB |
260 |
RCTL_GLOBAL_SECONDS |
seconds |
s |
1 |
|
Ks |
103 |
|
Ms |
106 |
|
Gs |
109 |
|
Ts |
1012 |
|
Ps |
1015 |
|
Es |
1018 |
RCTL_GLOBAL_COUNT |
count |
none |
1 |
|
K |
103 |
|
M |
106 |
|
G |
109 |
|
T |
1012 |
|
P |
1015 |
|
E |
1018 |
Scaled values can be used with resource controls. The following example shows a
scaled threshold value:
task.max-lwps=(priv,1K,deny)
Note - Unit modifiers are accepted by the prctl, projadd, and projmod commands. You
cannot use unit modifiers in the project database itself.
Resource Control Values and Privilege Levels
A threshold value on a resource control constitutes an enforcement point where local
actions can be triggered or global actions, such as logging, can occur.
Each threshold value on a resource control must be associated with a privilege
level. The privilege level must be one of the following three types.
Basic, which can be modified by the owner of the calling process
Privileged, which can be modified only by privileged (superuser) callers
System, which is fixed for the duration of the operating system instance
A resource control is guaranteed to have one system value, which is defined
by the system, or resource provider. The system value represents how much of
the resource the current implementation of the operating system is capable of providing.
Any number of privileged values can be defined, and only one basic
value is allowed. Operations that are performed without specifying a privilege value are assigned
a basic privilege by default.
The privilege level for a resource control value is defined in the
privilege field of the resource control block as RCTL_BASIC, RCTL_PRIVILEGED, or RCTL_SYSTEM. See setrctl(2)
for more information. You can use the prctl command to modify values that are
associated with basic and privileged levels.
Global and Local Actions on Resource Control Values
There are two categories of actions on resource control values: global and local.
Global Actions on Resource Control Values
Global actions apply to resource control values for every resource control on the
system. You can use the rctladm command described in the rctladm(1M) man page to
perform the following actions:
You can disable or enable the global logging action on resource controls. You
can set the syslog action to a specific degree by assigning a severity
level, syslog=level. The possible settings for level are as follows:
debug
info
notice
warning
err
crit
alert
emerg
By default, there is no global logging of resource control violations. The level
n/a indicates resource controls on which no global action can be configured.
Local Actions on Resource Control Values
Local actions are taken on a process that attempts to exceed the control
value. For each threshold value that is placed on a resource control, you
can associate one or more actions. There are three types of local actions:
none, deny, and signal=. These three actions are used as follows:
- none
No action is taken on resource requests for an amount that is greater than the threshold. This action is useful for monitoring resource usage without affecting the progress of applications. You can also enable a global message that displays when the resource control is exceeded, although the process exceeding the threshhold is not affected.
- deny
You can deny resource requests for an amount that is greater than the threshold. For example, a task.max-lwps resource control with action deny causes a fork system call to fail if the new process would exceed the control value. See the fork(2) man page.
- signal=
You can enable a global signal message action when the resource control is exceeded. A signal is sent to the process when the threshold value is exceeded. Additional signals are not sent if the process consumes additional resources. Available signals are listed in Table 6-3.
Not all of the actions can be applied to every resource control.
For example, a process cannot exceed the number of CPU shares assigned to
the project of which it is a member. Therefore, a deny action is
not allowed on the project.cpu-shares resource control.
Due to implementation restrictions, the global properties of each control can restrict the
range of available actions that can be set on the threshold value. (See
the rctladm(1M) man page.) A list of available signal actions is presented in
the following table. For additional information about signals, see the signal(3HEAD) man page.
Table 6-3 Signals Available to Resource Control Values
Signal |
Description |
Notes |
|---|
SIGABRT |
Terminate
the process. |
|
SIGHUP |
Send a hangup signal. Occurs when carrier drops on an open
line. Signal sent to the process group that controls the terminal. |
|
SIGTERM |
Terminate the process.
Termination signal sent by software. |
|
SIGKILL |
Terminate the process and kill the program. |
|
SIGSTOP |
Stop the
process. Job control signal. |
|
SIGXRES |
Resource control limit exceeded. Generated by resource control facility. |
|
SIGXFSZ |
Terminate
the process. File size limit exceeded. |
Available only to resource controls with the
RCTL_GLOBAL_FILE_SIZE property (process.max-file-size). See rctlblk_set_value(3C) for more information. |
SIGXCPU |
Terminate the process. CPU time limit
exceeded. |
Available only to resource controls with the RCTL_GLOBAL_CPUTIME property (process.max-cpu-time). See rctlblk_set_value(3C) for
more information. |
Resource Control Flags and Properties
Each resource control on the system has a certain set of associated properties.
This set of properties is defined as a set of flags, which
are associated with all controlled instances of that resource. Global flags cannot be modified,
but the flags can be retrieved by using either rctladm or the getrctl
system call.
Local flags define the default behavior and configuration for a specific threshold value
of that resource control on a specific process or process collective. The local
flags for one threshold value do not affect the behavior of other defined
threshold values for the same resource control. However, the global flags affect the
behavior for every value associated with a particular control. Local flags can be
modified, within the constraints supplied by their corresponding global flags, by the
prctl command or the setrctl system call. See setrctl(2).
For the complete list of local flags, global flags, and their definitions, see
rctlblk_set_value(3C).
To determine system behavior when a threshold value for a particular resource control
is reached, use rctladm to display the global flags for the resource control
. For example, to display the values for process.max-cpu-time, type the following:
$ rctladm process.max-cpu-time
process.max-cpu-time syslog=off [ lowerable no-deny cpu-time inf seconds ]The global flags indicate the following.
- lowerable
Superuser privileges are not required to lower the privileged values for this control.
- no-deny
Even when threshold values are exceeded, access to the resource is never denied.
- cpu-time
SIGXCPU is available to be sent when threshold values of this resource are reached.
- seconds
The time value for the resource control.
- no-basic
Resource control values with the privilege type basic cannot be set. Only privileged resource control values are allowed.
- no-signal
A local signal action cannot be set on resource control values.
- no-syslog
The global syslog message action may not be set for this resource control.
- deny
Always deny request for resource when threshold values are exceeded.
- count
A count (integer) value for the resource control.
- bytes
Unit of size for the resource control.
Use the prctl command to display local values and actions for the resource
control.
$ prctl -n process.max-cpu-time $$
process 353939: -ksh
NAME PRIVILEGE VALUE FLAG ACTION RECIPIENT
process.max-cpu-time
privileged 18.4Es inf signal=XCPU -
system 18.4Es inf none The max (RCTL_LOCAL_MAXIMAL) flag is set for both threshold values, and the inf
(RCTL_GLOBAL_INFINITE) flag is defined for this resource control. An inf value has an infinite
quantity. The value is never enforced. Hence, as configured, both threshold quantities represent
infinite values that are never exceeded.
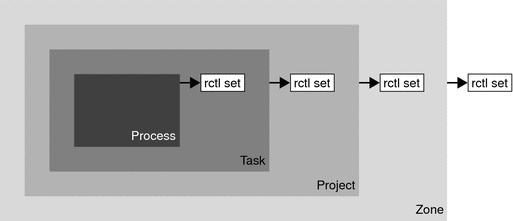
Resource Control Enforcement
More than one resource control can exist on a resource. A resource
control can exist at each containment level in the process model. If resource
controls are active on the same resource at different container levels, the smallest container's
control is enforced first. Thus, action is taken on process.max-cpu-time before task.max-cpu-time
if both controls are encountered simultaneously.
Figure 6-1 Process Collectives, Container Relationships, and Their Resource Control Sets
Global Monitoring of Resource Control Events
Often, the resource consumption of processes is unknown. To get more information, try
using the global resource control actions that are available with the rctladm command.
Use rctladm to establish a syslog action on a resource control. Then, if any
entity managed by that resource control encounters a threshold value, a system message
is logged at the configured logging level. See Chapter 7, Administering Resource Controls (Tasks) and the rctladm(1M)
man page for more information.
